Join the Community &
Begin Your Hunt, for FREE!
Get free and exclusive Community access to Cyborg Security's threat hunting content platform, HUNTER and get access to dozens of advanced behavioral threat hunting content packages that you can deploy in your environment today!
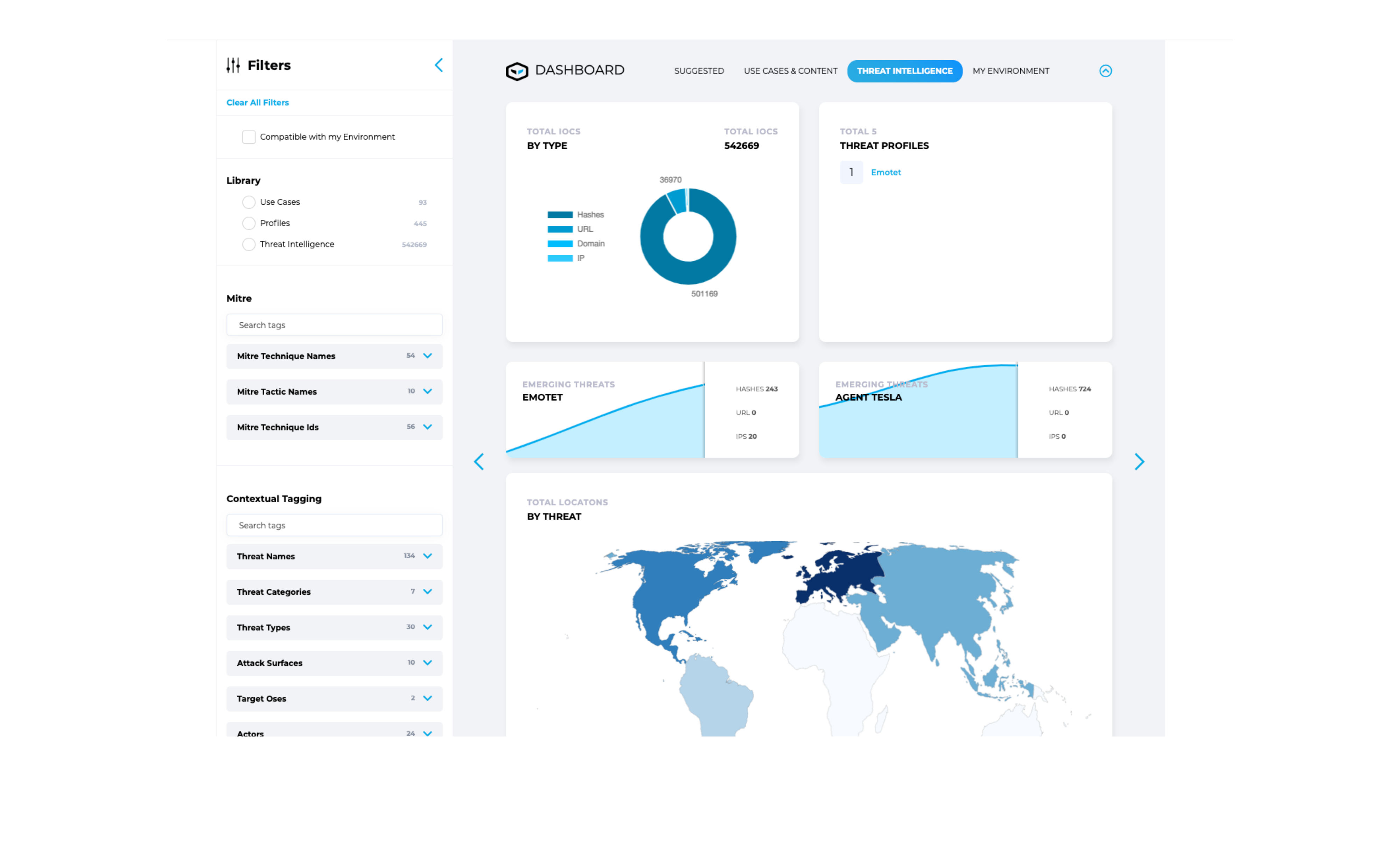
How Security Teams are Benefiting with HUNTER
.png?width=4000&height=2417&name=HUNTER%20-%20Threat%20Intelligence%20(1).png)
Build or Mature Your Threat Hunting Operations
- Enables hunt teams to deploy more threat hunts at scale faster and more consistently and repeatably.
- Ensure your threat hunters can stay focused on the hunt and get rid of the ‘busy work’ of the pre-hunt.
- Eliminates time consuming and complicated research, development, documentation. and constant review.
- Empowers hunters and intelligence teams to truly operationalize third party reporting.
- Expedites hunting for emerging threats and advanced adversaries.
- Effortlessly deploy a turnkey threat hunting programme.
- Efficiently transition true positive hunts into repeatable detections with transparent research and analyst notes.
- Immediately upskill new and novice hunters into advanced hunt teams
From Blue Team to Hunt Team
- Upskill or re-skill existing security analysts into threat hunters.
- Guide analysts through every hunt with analyst-focused run books.
- Close the gap on consistent remediation with battle-tested mitigation recommendations.
- Enable SOCs to proactively hunt for suspicious and malicious behaviors when responding to incidents.
- Expand hunting capabilities to behaviors and tactics, beyond fragile and unreliable indicators of compromise
.png?width=4000&height=2417&name=HUNTER%20-%20Threat%20Intelligence%20(1).png)
Detection-as-Code for Content Engineers
- Extend existing content engineering resources.
- Decrease time to deployment with advanced content validation. Emulation, and simulation capabilities.
- Eliminate the need for engineering teams to constantly review and revalidate content.
- Effortlessly keep track of all staged and deployed content, including when content is updated.
Copyright © 2021 Cyborg Security Security, Inc. All Rights Reserved. Privacy Policy
.png?width=200&height=65&name=Untitled%20design%20(49).png)